There is a lot of information in the Threat Library. It can be overwhelming. How can you use the Threat Library in your life, in a particular project, or when carrying out actions? This tutorial is designed to help you navigate the Threat Library using attack trees[1].
Attack trees are a tool to facilitate a brainstorming exercise on the different ways an adversary could successfully attack you in a given context by representing the attacks — the threats — in a tree structure. They help understand how a plan or project is vulnerable to repression by modeling the options available to an adversary.
You can do this threat modeling exercise on your own, but, if you're planning to carry out an action with other people, we recommend that you do it with them. This exercise should benefit both inexperienced and experienced crews. Even if everyone already has strong security practices, it provides a structured way to ensure that no threats are overlooked and that everyone is on the same page about security expectations.
A simple example: skipping a school day
Let's start with a simple example before we consider a real one. You're a kid in school, and you and your buddy want to skip a day of school, but you don't want your parents to know. The adversary is the school system.
You start by drawing the root node: it represents the adversary's goal. In this example, the goal is to let your parents know that you skipped school. The school could call your parents or send them a letter. Or one of your professors could run into your respective parents and warn them — this could happen with your Math teacher who lives down your street, or your History teacher who plays Bingo with your buddy's parents every weekend. You draw all these nodes.
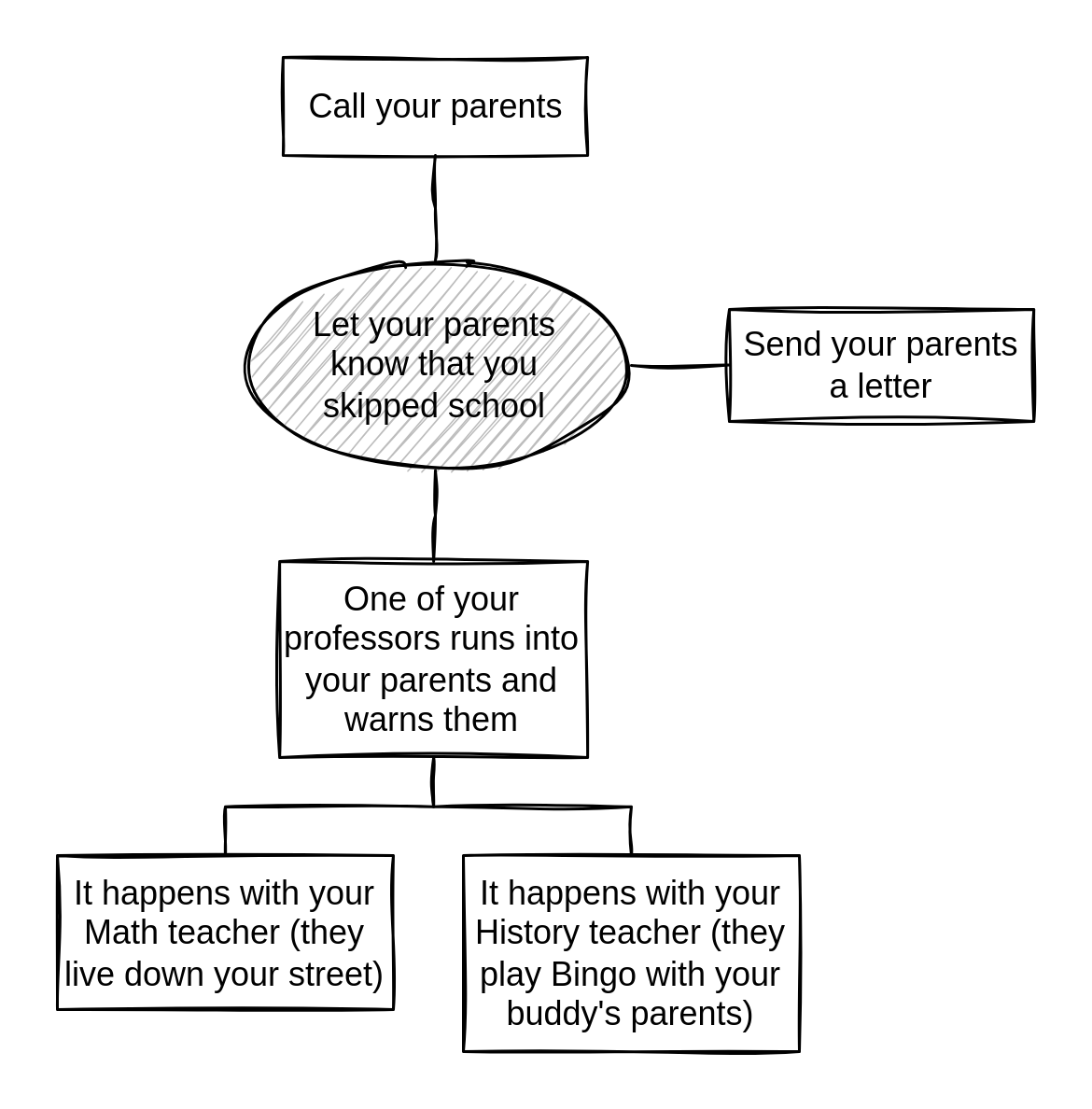
“Skipping school” attack tree
Notice that for a node to be true, one of its successors must be true. For example, for “Let your parents know that you skipped school” to be true, one of the three nodes around it must be true. For “One of your professors runs into your parents and warns them” to be true, one of the two nodes below it must be true. In other words, if you can trace a path from an outermost node to the root node where all the nodes along the path are true, that means that the root node is true, and the attack is complete.
So you and your buddy decide to skip a day when you don't have either Math or History. The night before you skip, you'll cut your parents' phone lines (blame it on the mice) and intercept their mail for the next few days. You're glad you came up with a great plan.
A real example: a riot in a big city in the United States
Let's say you and some comrades are preparing for a riot in a big city in the United States. You want to do some damage, but you don't want to get caught… You turn to the Threat Library for help. You print out the zine version of the Threat Library, take a pen and paper, and meet with your comrades outdoors and without electronic devices.
The goal of the discussion: draw an attack tree, identify techniques and mitigations that apply to your context, and decide how to implement those mitigations. After the riot, it may be a good idea to conduct an action review.
Draw the attack tree
In this example, the adversary is the State and its cops, and their goal is to get enough evidence of your involvement in the riots to convince a judge to convict you. You draw an attack tree to represent the ways they could achieve this goal[2]. You begin with the root node.
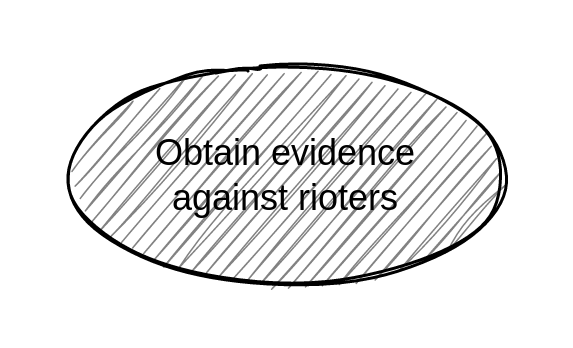
“Riot” attack tree (root node)
You then add the immediate nodes, next to the root node. At this stage, you should add anything you can think of, even if you're not sure it applies to your context. The tree can grow in all directions, to make it more compact.
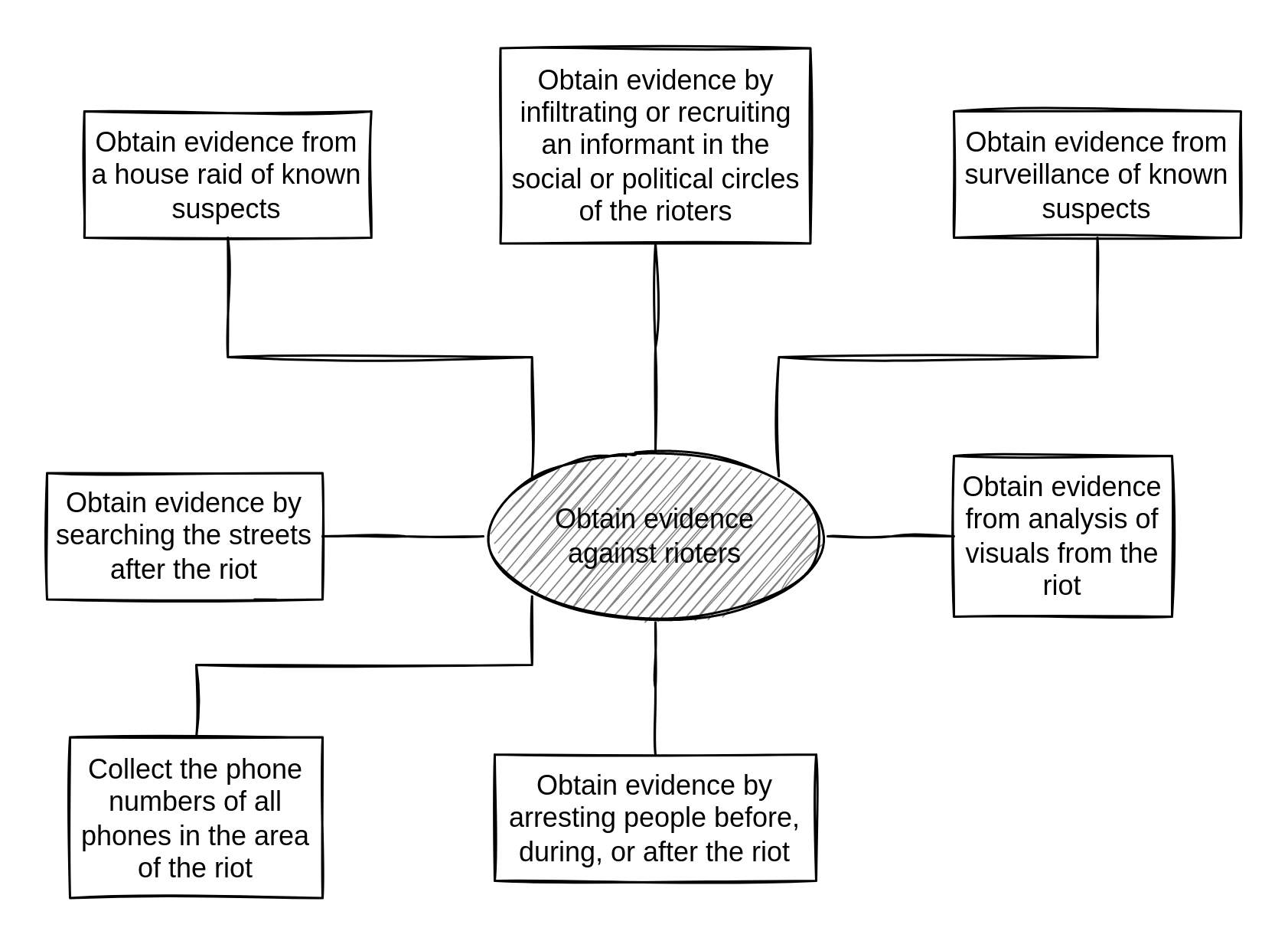
“Riot” attack tree (first nodes)
You use the Threat Library to help grow the tree — reading about techniques helps you better understand all the options available to your adversary. Creating attack trees requires a certain mindset and takes practice. The tree is complete when no more nodes are needed to complete an attack, and every attack that you can think of is represented.
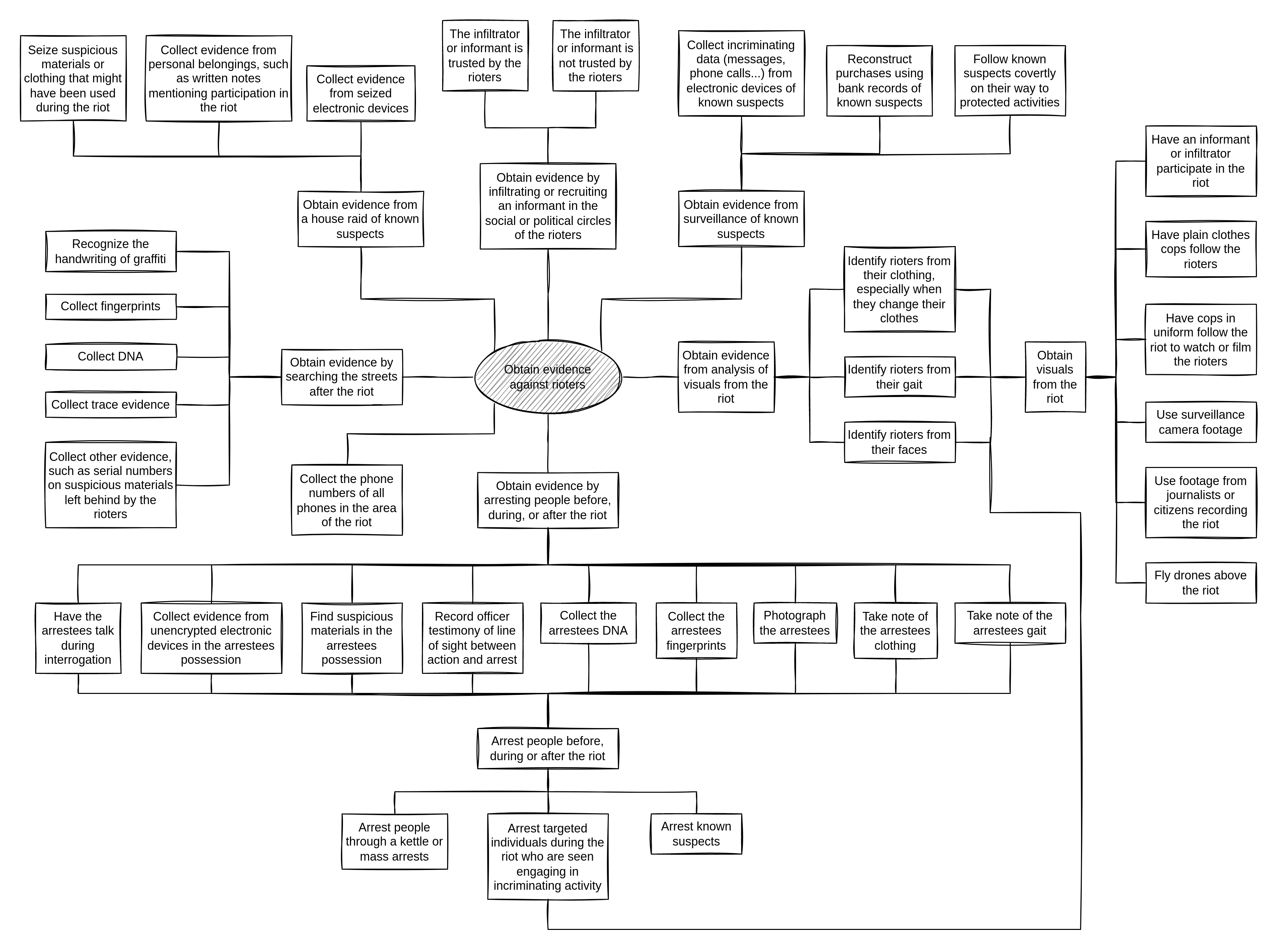
Identify techniques
You identify all techniques represented in the tree by matching nodes with techniques from the Threat Library. You do so branch by branch to avoid getting lost: it's best to start with nodes closer to the root node, and then work your way up the branch.
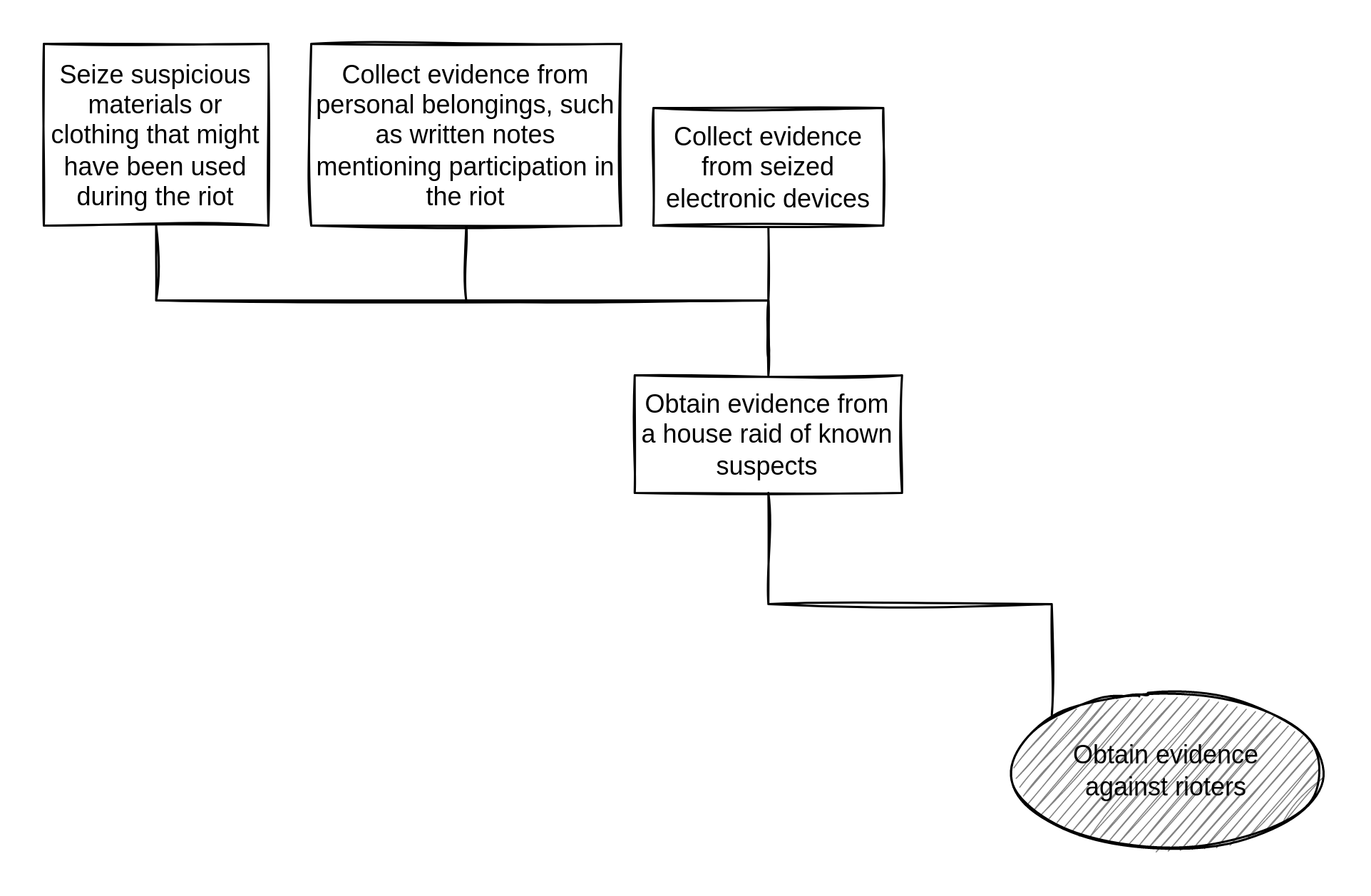
“Riot” attack tree (house raid branch)
You start with the “Obtain evidence from a house raid of known suspects” branch:
- “Obtain evidence from a house raid of known suspects” matches House raid.
- “Collect evidence from seized electronic devices” matches Targeted digital surveillance: Physical access because they would access your electronic devices, and Targeted digital surveillance: Authentication bypass, if they try to guess your passwords or break your encryption.
- The other nodes don't match anything, they're just part of the house raid.
At this stage, it can be useful to assess the risks of the techniques you're listing — this will inform whether and how thoroughly you should mitigate each of them. See the “Assessing Risk” section below for how to assess a technique's risk using the concepts of likelihood and impact.
Then you move on to the next branch until the whole tree is covered, building a table.
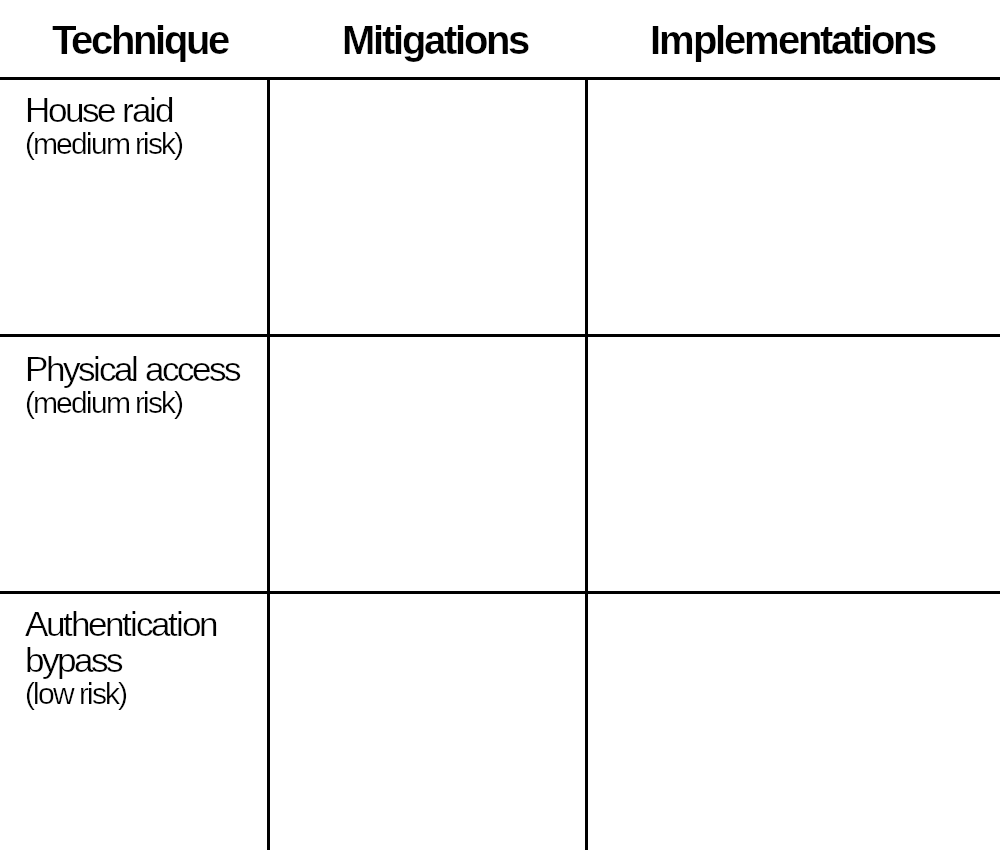
Beginning of the table.
Identify mitigations
Next, you identify all the mitigations that you want to implement by looking at the mitigations that the Threat Library suggests for the techniques in the table.
On our example branch, you decide to implement:
- For “House raid”, Preparing for repression, Preparing for house raids and Stash spot or safe house. You don't want to implement Clandestinity because you decide against going down that road.
- For the two “Targeted digital surveillance” techniques, Digital best practices is the only mitigation that makes sense in your context.
You update the table.
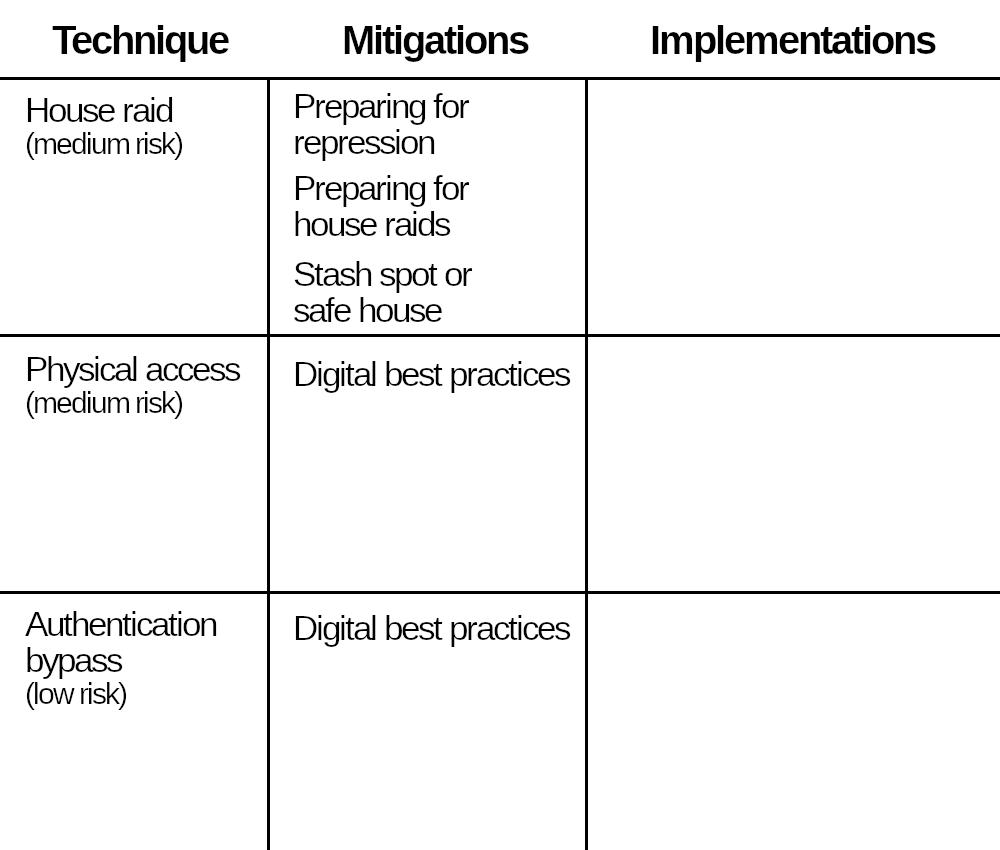
Beginning of the table, with mitigations.
Decide how to implement mitigations
Finally, you decide how to implement the mitigations in the table. Reading their entries in the Threat Library can give you some ideas. The risk you assessed for each technique helps you to know how much energy to put into the mitigations. You decide on the following implementations:
- “Preparing for repression”: since you and your comrades all live in the same place, there is a risk that you will all be arrested after a house raid. You will make sure that other comrades know how to support you if this happens.
- “Preparing for house raids”: you decide to stop storing the fireworks under your bed.
- “Stash spot or safe house”: you decide to bury a waterproof container in a nearby forest to store the fireworks. When one of you accesses it, they must wear gloves and make sure there's no one around.
- “Digital best practices”: your devices are already encrypted, and you're not using them to talk about the riots anyway. You have to find out if a phone's encryption works when it's turned on and locked because you're not sure.
At this stage, it can be useful to re-assess the risks of the techniques to make sure that they have been sufficiently lowered by the mitigations you have decided to implement.
You update the table.
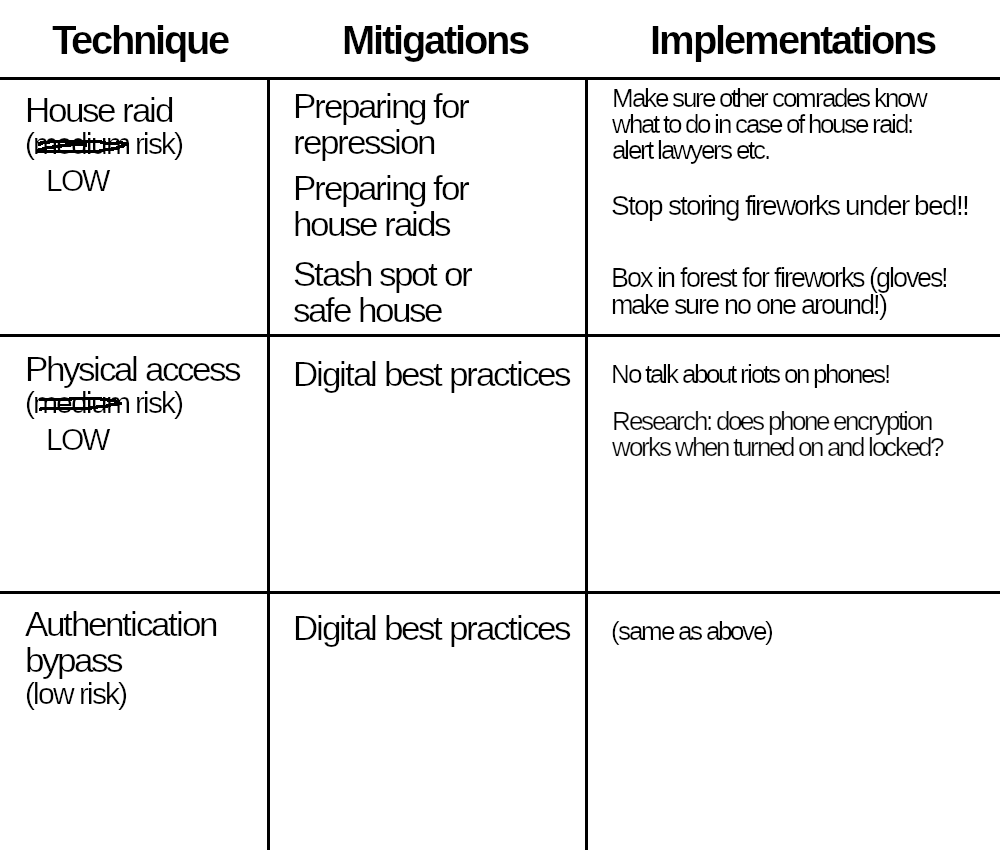
Beginning of the table, with mitigations and their implementations.
Burn or digitize your notes
The notes taken during this threat modeling exercise should not be kept around because they could be considered evidence of conspiracy. You have two options:
- At the end of the exercise, memorize your notes and then burn them. This approach makes it difficult to later revisit your notes and expand them.
- At the end of the exercise, digitize your notes by manually copying them to an encrypted USB device using Tails[3] (remember to follow digital best practices). You can use Libreoffice Draw (included in Tails by default) to draw the attack tree. Once the notes are digitized, they shouldn't be printed out because this could leave a trace on the printer, but they can be manually copied to paper again so you can revisit them away from a computer.
Perform an action review
After the riot, you and your comrades take some time to conduct an action review: in outdoor and device-free conversations, you discuss what went well and what went wrong, and whether there is room for improvement in the coverage of your attack tree or how you implemented the mitigations.
Assessing risk
Risk is the combined measure of a technique's impact and likelihood. If a technique would have a high impact, but is very unlikely to be used, it might be considered low risk. If a technique would have a medium impact, but is likely to be used, it might be considered high risk. If you consider the risk of a technique to be high, it means that you should apply mitigations for it more thoroughly.
For example, in most contexts, if you are planning to commit arson, the Forensics: DNA technique is high risk. This is because it has a high impact (a good DNA match to an arson crime scene is solid evidence in court) and a high likelihood (in most contexts, DNA forensics is systematically used in arson investigations).
Impact
Impact is a measure of the consequences if a technique is used. It depends on the tactic:
- Deterrence tactic: Impact is determined by whether the target is successfully deterred.
- Incrimination tactic: Impact is determined by how “solid” the evidence gathered is.
- Arrest tactic: Impact is determined by whether the target is successfully apprehended.
Likelihood
Likelihood is a measure of how likely it is that an adversary will attempt a technique.
Adversary resources increase risk
If more resources are devoted to the repression of an action, a given technique may be more likely to be used, increasing its likelihood, and be used more thoroughly, increasing its potential impact. Broadly speaking, more resources are devoted to the repression of an action if an adversary feels more threatened by it.
For example:
- In most contexts, DNA forensics is systematically used in arson investigations. If the adversary has limited resources, the search might be limited to obvious surfaces such as door handles. If the adversary has more resources — which can be the case if the arson caused a lot of damage — the crime scene is more likely to be extensively searched for DNA evidence.
- In most contexts, if the adversary is the State, actions that are classified as “terrorism” or “threats to national security” will receive an extraordinary amount of resources. The State may devote many resources to actions that took place during an uprising, because the uprising was seen as a threat to the integrity of the State.
Mitigations decrease risk
By taking appropriate mitigations, you become less vulnerable to a technique, decreasing its potential impact.
For example, you are vulnerable to DNA forensics because your body constantly sheds DNA. If you apply DNA minimization protocols when committing arson, you become less vulnerable to DNA forensics.
Risk and local context
Understanding the habits and motivations of an adversary in repressing an action can help you to infer the range of repressive techniques they are likely to use, and how thoroughly they will use them. The repressive operations can help you gain an understanding of how a given technique is used in a given context.
Additional tips on using the Threat Library
The Threat Library home page provides an overview of all tactics and techniques, as well as buttons that allow you to hide or show specific techniques. For example, you might want to show only techniques that fit your threat model to better visualize the techniques that might apply to your context. If you follow our suggested process above and draw your own attack tree, the overview can help you think of relevant techniques that are missing from your tree.
The Threat Library welcomes external contributions, such as:
- Changes to existing techniques, mitigations or repressive operations.
- Suggesting the addition of new techniques, mitigations or repressive operations.
- Attack trees for different types of projects.
- Translating the Threat Library to new languages.
See the contribute page for more information.
For another approach to threat modeling that can also serve as a tutorial to the Threat Library, see Threat Modeling Fundamentals.
For complex actions, you may want to make a temporal distinction and draw an attack tree for each step of the action (e.g. planning, preparation, execution, dissolution).

